
Brand content protection
April 20, 2020
Tech Leaks : how serial leakers operate, how to fight as a brand
While technology fans are fond of product Leaks, brands are much less ! Learn more about the methods used by the perpetrators and how to fight back, brand side, to avoid disastrous consequences.
Quick read :
Pros Leakers and their methods
Consequences on brands' side
How to fight against leaks
While technology fans are fond of product leaks, brands are much less ! Learn more about he methods used by the perpetrators and how to fight back, brand side to avoid disastrous consequences.
The success of your brand generates all kinds of desires, and not necessarily all in your best interest. Pros Leakers do not seek to ruin you but to take advantage of your notoriety. For proof, they explicitly sign their deeds with a watermark on the visuals unveiled by them ! They thus create their own brand by parasitizing your value.

Serial leaker methods
If your product was a "person" star, leakers would be waiting at the entrance of your building, on the lookout, with a telephoto lens, and would dig in your trash. But since it's a famous brand exposed on the internet, it's a bit different :
Declarations to regulatory agencies
Firstly, they patiently watch for your filings to regulatory agencies (TENAA in China, FCC in the US, Patent office ...). They search for your diagrams and standardized labels for clues to the new characteristics of your next product.

Prototypes escaped from the labs
Secondly, leakers manage to get photos of prototypes sneaked out of the labs. These models may be masked in temporary shells or "protected" by labels indicating "do not leak" (naivety or cynical staging ?). They are sufficiently recognizable to learn about new features like screen size, the number of lenses, and much more.

Gaffes of online shops
Further, they are on the lookout for recurring blunders from online retailers, who feverishly prepare their virtual brochures before the official launch of the product. In a rush to be ready on time, their secrecy process does not yet seem quite well crafted. As a case and point, these recent articles on the furtive appearance of electronic equipment on online stores.

3D renderings and marketing materials escaped from insufficiently secure processing chains
"There has been no smartphone or gadget released in the past couple of years without seeing renders or actual images on Twitter or YouTube first, and so far, leakers have been hiding behind their anonymity". (B.Toulas in "Invisible Image Watermarks to Change the Tech Leak Landscape" on Technadu.com)
Other types of visuals manage to escape: 3D renderings of products soon to be launched. Computer graphics renders are available before an actual product is made and very often of superior quality to the photographs of the finished product. They generally travel between creative and marketing teams to be enriched with promotional messages, packaging design, and catalogs layout. Exchanges are done internally or with external suppliers, via email, DAM, WeTransfer, Dropbox, depending on the tools used by the service provider or the company.
You would certainly like to know by which mean your image landed in the hands of this famous leaker...

Hero or scourge ?
Heroes, really ? Let's ask product managers, creative ops, brand managers and test technicians whose work is ruined, integrity questioned, sales compromised and competitive advantage seriously undermined ?
Most fans of the brand find these leaks useful, assuming that they reinforce its notoriety. Even they think that they are intentional. But for many of the companies we work with, we know it isn't the case.
Many industries are affected
In the consumer electronics industry like the automotive sector, leaks on new models drive sales of models still on the shelves down. People stop buying, waiting for the newest model to be available (as it has been the case for Apple with an unexpected iPhone sales fall on leaks about new model).
In the apparel and luxury goods industries, counterfeiting is the most prevalent use of product leakage of visuals.
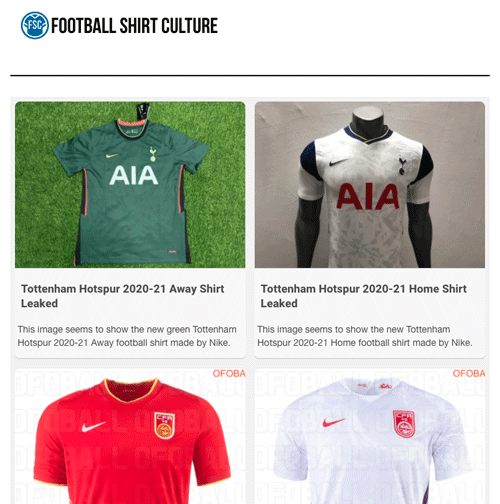
Many brands prefer to communicate on their own
Moreover, brands generally prefer to control their communication and their product launches themselves.
"We want the chance to tell our customers why the product is great, and not have that done poorly by someone else," Greg Joswiak, an Apple product marketing executive, said in an internal memo warning employees to stop leaking information to media.
But brands that try to fight back by taking the lead over leaks with early announcements often find themselves losing out and fail their launch.
"When you're a long way out from releasing a product there's also the risk of a failure to launch. Take Apple's AirPower for example." (K.Carlon in "The problem with product leaks" on Android Authority).
However, is a leak the result of an offense or negligence ? While the journalist investigates, the brand must protect itself ; everyone has their role to play. As there are many reasons why tech leaks happen, it is up to the brand to implement the solution necessary to secure them judiciously.
How to fight against leaks ?
As long as statements to the communications regulators are publicly available, we can't prevent snoopers from finding what they're looking for. Sorry !
As for leaks of prototypes from outside vendors: again, no need for advance science. While you cannot expect to find the fingerprints of the guilty party on the photo - we are not in the movies after all - there are ways to protect oneself. Replacing the "do not leak" label with a QRCode indicating the prototype identifier and keeping an allocation register for these prototypes seems to be a good start.
Auditing visuals throughout their creation, retouching, enrichment, and sharing, is, however, the most effective process:
Step #1 : Use digital watermarking techniques to find the source
At IMATAG, we get incoming requests every day from professionals whose activity is deeply affected by leaks, and who suffer from not being able to trace them. The most tech-savvy know the advantages of invisible watermarking secretly inserted into an image and turn on via our Imatag Leaks solution. Be careful : a simple invisible watermark will not do the trick.
- It must be really invisible. Luis Q., creative at a large brand of Smartphones, chose IMATAG after comparing its imperceptibility to other watermarks on the market. In essence, it was the only one to respect the perfect gradient of his 3D renderings.

- Then it must be able to differentiate several copies of the same image. Imagine sending the same embargoed visual to 15 journalists. You will have to "mark" the same image 15 times, ie, produce 15 visually identical unique images, each secretly carrying the identifier of each recipient.

One image, three identical copies, but actually different !
- Finally, it must resist the many "attacks" that images and videos on the internet undergo (crop, resize, compression, color changes, etc.).

How to fight leaks with an invisible watermark ?
When you have integrated your marking solution in all the "risky" stages of your workflow :
- Mark your images for each destination
- Watch the web and especially the most frequent sources of Leaks (see below)
- As soon as a leak appears, detect the watermark present in the image and reveal its original recipient and, thus, the source of the leak.
Step #2 : Monitor the web and especially the frequent sources of leaks
Pro Leakers do not hide. They are stars. Monitoring their social accounts is not difficult if you have significant resources! Instead, opt for an excellent automated monitoring solution able to crawl specific images and videos with a 100% reliable result. Be careful, here too ; a simple reverse engine will not be enough.
- Your image tracking solution must be capable of specific crawling (harvesting content from targeted sources). Standard solutions like TinEye or Google Image match your visuals with a database of web images. These bases are certainly huge but formed randomly. Like a needle in a haystack, it can take months for your visual content to be detected. If you fear leaks, you need a solution capable of targeting the most "risky" sites, and also the blogs and social accounts on which our leaksters generally reveal their findings.
- The solution must work with still images but also videos. If your image appears in a Youtube channel or 3 seconds of your promotional video have been included in a video montage, you should also be able to find it.
- Finally, demand a 100% reliable visual recognition capability. Most Brand Protection or Visual Search offers on the market do not have sufficiently reliable visual recognition technology, they generally require human verification. Only Imatag uses its watermark to certify that an image is indeed identical to an original, and can even detect modifications.
Most of the solutions on the market do not have sufficiently reliable visual recognition technology. They generally require human verification. Only IMATAG uses its watermark to certify that an image is identical to an original.
What’s next ?
The scientific name for content identification technology is “traitor tracing”. Still, we rarely use it because no one likes traitors and even less having to report them. In fact, this technology should allow you to locate failures or negligence in your internal and external processes, from the production of content to their distribution, rather than turning you into a revengeful vigilante. It is mainly a question of proving to all the players in the chain that an effective invisible tracking technology protects your visual content.
This information will deter potential sources of leakage. It will remind everyone of the importance of sensitive content and their responsibility to keep it secret.
.jpg)
Agency's Guide to preparing Leak-proof campaigns
Tips, do's and dont's for professionals involved in preparing for launch campaigns.
Download your copyThese articles may also interest you

Brand content protection
July 27, 2023
From Notoriety to Leaks: The Ambivalent Role of Influencers and Their Communities

Brand content protection
June 6, 2023
Optimizing Brand Monitoring: Social Listening Meets Digital Watermarking

Brand content protection
May 11, 2023









